

I find it very difficult to recommend generative ai as a learning tool (specifically for juniors) as it often spits out terrible code (or even straight up not working) which could be mistaken as “good” code. I think the more experienced a dev is, the better it is to use more like a pair programmer.
The problem is it cannot go back and correct/improve already generated output unless prompted to. It is getting better and better, but it is still an overly glorified template generator, for the most part, that often includes import statements from packages that don’t exist, one off functions that could have been inline (cannot go back and correct itself), and numerous garbage variables that are referenced only once and take up heap space for no seemingly no good reason.
Mainly speaking on GPT4, CoPilot is better, both have licensing concerns (of where did it get this code from) if you are creating something real and not for fun.







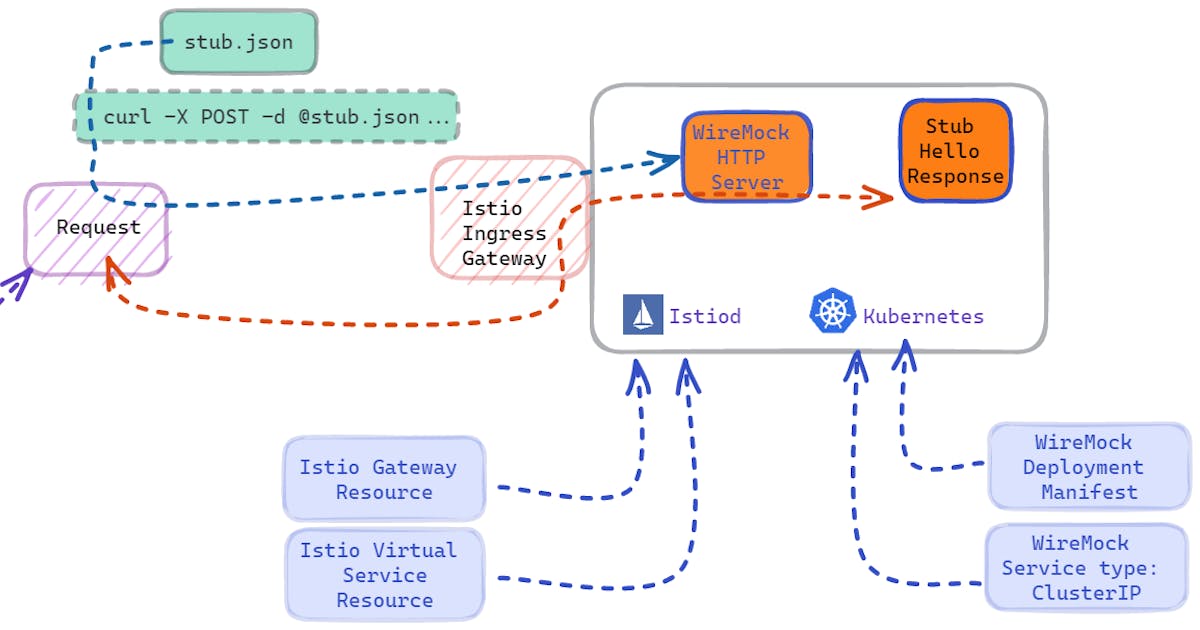
Thanks for sharing! I definitely hadn’t seen that plugin. We definitely use helm, even though I hate it lol. I will take a look when I get around to looking at external secrets since I still haven’t had a chance to (you know how it goes… priorities made up by some random PM or whatever)